Cara Install .NET Framework 3.5 di Windows 10
.NET Framework adalah kumpulan system library yang dibutuhkan
beberapa aplikasi Windows. Tanpa adanya .NET Framework, aplikasi di
Windows tidak bisa dijalankan dan akan menyebabkan error.
Pada Windows 8 & Windows 10, Microsoft tidak menginstall secara langsung .NET Framework 3.5. Sebenarnya, .NET
Framework 3.5 sudah ada didalam file ISO Windows 10 yang kalian gunakan
untuk install, tinggal kalian install saja lewat file ISO tersebut.
Kalian bisa lihat caranya dibawah ini.
Sebelum mulai menginstall, kalian pastikan memiliki persyaratan dibawah :
- File ISO Windows 10 yang kalian gunakan untuk install, pastikan kalian menggunakan file ISO yang sama dengan Build Number yang sama & Arsitektur bit yang sama ( maksudnya jangan gunakan file ISO Windows 10 x86 untuk menginstall .NET Framework 3.5 di Windows 10 64-bit ! ).
- Sangat disarankan untuk menginstall .NET Framework 3.5 di Windows 10 dalam keadaan masih fresh install. Artinya, Windows 10 tersebut belum diinstall update sama sekali.
Cara Install .NET Framework 3.5 di Windows 10
1. Mount file ISO Windows 10 dengan Daemon Tools atau masukkan DVD file ISO Windows 10 kedalam PC kalian.
2. Buka Command Prompt dan jalankan sebagai Administrator, setelah itu pada CMD kalian ketik perintah dibawah ini :
Dism /online /enable-feature /featurename:NetFX3 /All /Source:D:\sources\sxs /LimitAccess
Perhatikan drive letter D yang saya beri warna merah, drive letter tersebut
menunjukan lokasi tempat disk drive kalian ( DVD-ROM atau Virtual
DVD-ROM ). Driver Letter bisa berbeda-beda, jadi kalian sesuaikan saja.
3. Jika sudah selesai maka akan muncul pesan dibawah ini.
4. Bagaimana ? Mudah bukan install .NET Framework 3.5 Offline di Windows
10 ? sekarang kalian bisa menjalankan aplikasi yang membutuhkan .NET
Framework 3.5 :)
source: http://www.software182.com/2015/07/cara-install-net-framework-35-di-windows-10.html#axzz3sa1FOCPR






 We
had a system come in recently that had been heavily infected by the
ZBot rootkit and a variety of Trojans. MS Security Essentials had
cleaned some things off, but the system still had a lot of junk on it.
The main problem, however, was the computer could not access the
Internet. Many virus infections create proxy servers and then set
Windows to route all web traffic through the virus proxy. When most
anti-virus programs kill off a virus like this, they don’t clear the
proxy setting. So you have no virus, but you also can’t access the
Internet. This is understandable since messing with that proxy setting
is dicey in a corporate environment where they get used heavily.
We
had a system come in recently that had been heavily infected by the
ZBot rootkit and a variety of Trojans. MS Security Essentials had
cleaned some things off, but the system still had a lot of junk on it.
The main problem, however, was the computer could not access the
Internet. Many virus infections create proxy servers and then set
Windows to route all web traffic through the virus proxy. When most
anti-virus programs kill off a virus like this, they don’t clear the
proxy setting. So you have no virus, but you also can’t access the
Internet. This is understandable since messing with that proxy setting
is dicey in a corporate environment where they get used heavily.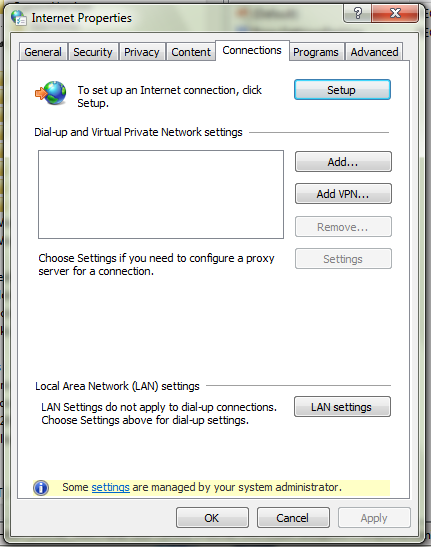 This
user account had Admin rights, so that seemed strange. After some
Google research, I came across some others who had the same issue and
This
user account had Admin rights, so that seemed strange. After some
Google research, I came across some others who had the same issue and